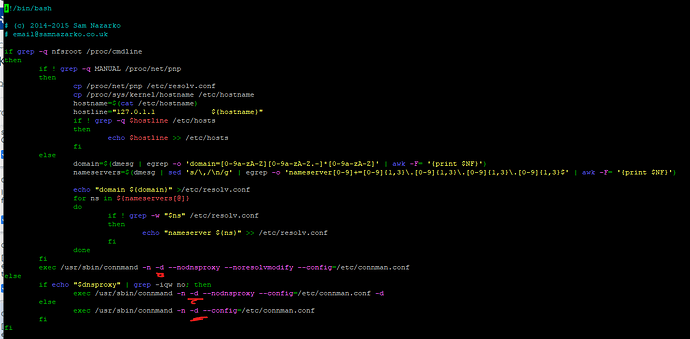
I want to create a WiFi network based on the ethernet connection
I’ve got the latest version of osmc on my Raspberry Pi 3B that is connected to Internet via Ethernet cable
I first went Settings → My OSMC → Network → Tethering → Enable
then looked up also by command line:
and I cannot connect to this network
there’s no log anywhere than anything went wrong
the connection just drops immediatly on mobile and tries reconnect and drops again
What should I do to grab some more info of what could go wrong?
You could check ifconfig. If your wired network is 192.168.0.x, the tether should be 192.168.1.x and vice versa.
eth0: flags=-28605<UP,BROADCAST,RUNNING,MULTICAST,DYNAMIC> mtu 1500
inet 192.168.1.155 netmask 255.255.255.0 broadcast 192.168.1.255
ether b8:27:eb:56:27:3f txqueuelen 1000 (Ethernet)
RX packets 1377725 bytes 491902977 (469.1 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1284658 bytes 278578726 (265.6 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 717 bytes 84145 (82.1 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 717 bytes 84145 (82.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
tether: flags=-28605<UP,BROADCAST,RUNNING,MULTICAST,DYNAMIC> mtu 1500
inet 192.168.0.1 netmask 255.255.255.0 broadcast 192.168.0.255
inet6 fe80::9c52:d7ff:fe63:2773 prefixlen 64 scopeid 0x20<link>
ether 9e:52:d7:63:27:73 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 153 bytes 46995 (45.8 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
wlan0: flags=-28605<UP,BROADCAST,RUNNING,MULTICAST,DYNAMIC> mtu 1500
ether b8:27:eb:03:72:6a txqueuelen 1000 (Ethernet)
RX packets 30903 bytes 8926935 (8.5 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 27313 bytes 7458602 (7.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
any ideas what I co do?
What you tried connecting on another device?
on Windows:

Do you have another OSMC device you can try connecting from?
Unfortunately, I don’t
Just tried tethering (ethernet to wifi) on my rpi 3b+ and got an ip with my android smart phone immediately.
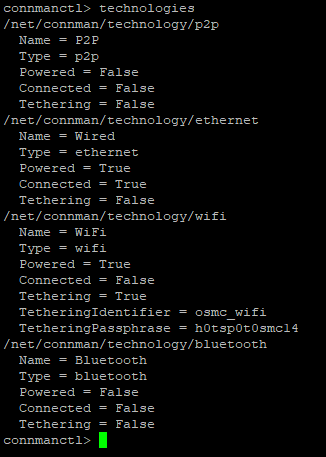
What you see in /var/lib/conmann? If there are folders starting with wifi… remove them.
There was one wifi saved there but I removed it now
but the issue remains
I’d be happy to set up some loggings to know what’s the deal here but I don’t event know where to start
I’d read somewhere about wpa_supplicant but I’m not sure if it’s used at all, since theres’ no config file:
Well, first difference I’ve noticed: You have a p2p technology mentioned, here I don’t have that enabled/visible.
Regarding logging: You could change /usr/bin/start-network and give every call of connmand the option -d in addition which give some debug info.
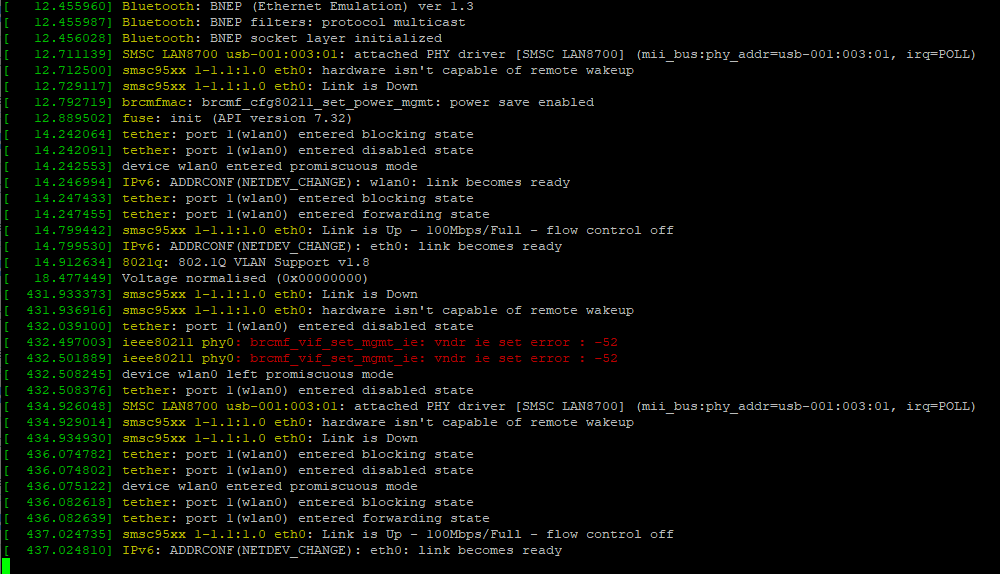
A dmesg -w lets you monitor the kernel messages when your device tries to connect to the tether wifi.
I’ve added debug flags to some places:
and the kernel messages output is here but doesn’t seem to be changing while connecting
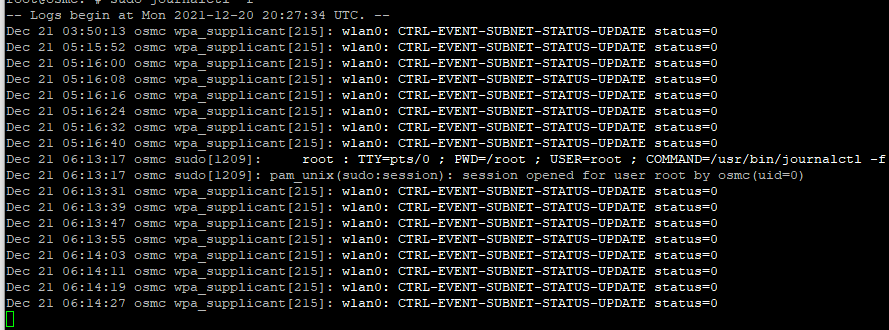
Sorry, my fault: Instead of dmesg -w use sudo journalctl -f
...
Dec 21 00:47:36 osmc-pi3 wpa_supplicant[362]: wlan0: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
Dec 21 00:47:36 osmc-pi3 wpa_supplicant[362]: wlan0: AP-STA-CONNECTED e6:54:18:8a:97:71
Dec 21 00:47:37 osmc-pi3 connmand[391]: DHCP server: Received DISCOVER
Dec 21 00:47:37 osmc-pi3 connmand[391]: DHCP server: find yiaddr 33597632
Dec 21 00:47:37 osmc-pi3 connmand[391]: DHCP server: lease_mac (nil) lease_nip (nil)
Dec 21 00:47:37 osmc-pi3 connmand[391]: DHCP server: Sending OFFER of 192.168.0.2
Dec 21 00:47:37 osmc-pi3 connmand[391]: DHCP server: Broadcasting packet to client
Dec 21 00:47:37 osmc-pi3 connmand[391]: DHCP server: Received REQUEST NIP -1062731774
Dec 21 00:47:37 osmc-pi3 connmand[391]: DHCP server: Sending ACK
Dec 21 00:47:37 osmc-pi3 connmand[391]: DHCP server: Sending ACK to 192.168.0.2
Dec 21 00:47:37 osmc-pi3 connmand[391]: DHCP server: Broadcasting packet to client
Dec 21 00:47:37 osmc-pi3 connmand[391]: DHCP server: lease_mac 0x12b4138 lease_nip 0x12b4138
Dec 21 00:47:38 osmc-pi3 connmand[391]: src/inet.c:icmpv6_rs_event()
Dec 21 00:47:38 osmc-pi3 connmand[391]: src/inet.c:icmpv6_rs_recv()
Dec 21 00:47:38 osmc-pi3 connmand[391]: src/inet.c:icmpv6_rs_recv() code 0 len 16 hdr 8
...
You can also increase the debug logging level of the wpa_supplicant by specifiying -d or the -dd in the call of wpa_supplicant at /lib/systemd/system/wpa_supplicant.service. Invoke a sudo systemctl deamon-reload followed by a sudo reboot, afterwards.
Only help I can give is how it looks like on my rpi 3B+ (it has another wifi chip than your rpi3 B) with active -d options for connmand and wpa_supplicant:
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: nl80211: Ignored event (cmd=19) for foreign interface (ifindex 3 wdev 0x0)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: nl80211: Drv Event 19 (NL80211_CMD_NEW_STATION) received for wlan0
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: nl80211: New station e6:54:18:8a:97:71
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: nl80211: Assoc Req IEs - hexdump(len=138): 00 0d 4e 65 75 4c 75 6d 6d 65 72 6c 61 6e 64 01 08 82 84 8b 96 24 30 48 6c 21 02 08 14 2d 1a 2d 01 13 ff 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 30 14 01 00 00 0f ac 04 01 00 00 0f ac 04 01 00 00 0f ac 02 00 00 32 04 0c 12 18 60 3b 14 51 51 53 54 73 74 75 76 77 78 79 7a 7b 7c 7d 7e 7f 80 81 82 46 05 73 10 91 00 04 7f 03 04 00 08 dd 07 00 50 f2 02 00 01 00 dd 08 8c fd f0 01 01 02 01 00
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wlan0: Event ASSOC (0) received
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: hostapd_logger: STA e6:54:18:8a:97:71 - associated
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: STA included RSN IE in (Re)AssocReq
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: New STA
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: ap_sta_add: register ap_handle_timer timeout for e6:54:18:8a:97:71 (300 seconds - ap_max_inactivity)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: nl80211: Set STA flags - ifname=wlan0 addr=e6:54:18:8a:97:71 total_flags=0x60 flags_or=0x0 flags_and=0xfffffff1 authorized=0
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: hostapd_logger: STA e6:54:18:8a:97:71 - event 1 notification
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wpa_driver_nl80211_set_key: ifindex=3 (wlan0) alg=0 addr=0x18feea8 key_idx=0 set_tx=1 seq_len=0 key_len=0
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: addr=e6:54:18:8a:97:71
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: nl80211: set_key failed; err=-22 Invalid argument)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: RSN: PTK removal from the driver failed
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: P2P: First non-P2P device connected
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: IEEE 802.1X: Ignore STA - 802.1X not enabled or forced for WPS
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: hostapd_logger: STA e6:54:18:8a:97:71 - start authentication
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: e6:54:18:8a:97:71 WPA_PTK entering state INITIALIZE
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wpa_driver_nl80211_set_key: ifindex=3 (wlan0) alg=0 addr=0x18feea8 key_idx=0 set_tx=1 seq_len=0 key_len=0
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: addr=e6:54:18:8a:97:71
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: nl80211: set_key failed; err=-22 Invalid argument)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: RSN: PTK removal from the driver failed
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: nl80211: Set STA flags - ifname=wlan0 addr=e6:54:18:8a:97:71 total_flags=0x60 flags_or=0x0 flags_and=0xfffffffe authorized=0
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: hostapd_logger: STA e6:54:18:8a:97:71 - unauthorizing port
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: e6:54:18:8a:97:71 WPA_PTK_GROUP entering state IDLE
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: e6:54:18:8a:97:71 WPA_PTK entering state AUTHENTICATION
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: e6:54:18:8a:97:71 WPA_PTK entering state AUTHENTICATION2
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Re-initialize GMK/Counter on first station
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: GMK - hexdump(len=32): [REMOVED]
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: Key Counter - hexdump(len=32): [REMOVED]
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: GTK - hexdump(len=16): [REMOVED]
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wpa_driver_nl80211_set_key: ifindex=3 (wlan0) alg=3 addr=0x614434 key_idx=1 set_tx=1 seq_len=0 key_len=16
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: nl80211: KEY_DATA - hexdump(len=16): [REMOVED]
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: broadcast key
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Assign ANonce - hexdump(len=32): 16 85 90 2f a7 96 3d 24 6f f8 55 5b 90 b2 7e 12 50 d4 38 5a 03 97 8d 85 0f b3 2c f6 36 9e 05 0d
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: e6:54:18:8a:97:71 WPA_PTK entering state INITPSK
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: Searching a PSK for e6:54:18:8a:97:71 prev_psk=(nil)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: Searching a PSK for e6:54:18:8a:97:71 prev_psk=(nil)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: e6:54:18:8a:97:71 WPA_PTK entering state PTKSTART
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: hostapd_logger: STA e6:54:18:8a:97:71 - sending 1/4 msg of 4-Way Handshake
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Send EAPOL(version=2 secure=0 mic=0 ack=1 install=0 pairwise=1 kde_len=0 keyidx=0 encr=0)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Replay Counter - hexdump(len=8): 00 00 00 00 00 00 00 01
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Use EAPOL-Key timeout of 1000 ms (retry counter 1)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wlan0: hostapd_new_assoc_sta: reschedule ap_handle_timer timeout for e6:54:18:8a:97:71 (300 seconds - ap_max_inactivity)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wlan0: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: l2_packet_receive_br: src=b8:27:eb:27:bd:07 len=113
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wlan0: RX EAPOL from b8:27:eb:27:bd:07 to e6:54:18:8a:97:71 (bridge - not for this interface - ignore)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: l2_packet_receive_br: src=e6:54:18:8a:97:71 len=135
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wlan0: RX EAPOL from e6:54:18:8a:97:71 to b8:27:eb:27:bd:07 (bridge)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wlan0: RX EAPOL from e6:54:18:8a:97:71
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: IEEE 802.1X: 121 bytes from e6:54:18:8a:97:71
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: IEEE 802.1X: version=1 type=3 length=117
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Received EAPOL-Key from e6:54:18:8a:97:71 key_info=0x10a type=2 mic_len=16 key_data_length=22
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Received Key Nonce - hexdump(len=32): d5 f9 a4 80 6a 47 6a cf 2c 82 a6 6b 98 c5 6d 27 aa cd 1b 0b 80 9e 99 90 b6 88 49 e8 88 e2 03 57
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Received Replay Counter - hexdump(len=8): 00 00 00 00 00 00 00 01
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: hostapd_logger: STA e6:54:18:8a:97:71 - received EAPOL-Key frame (2/4 Pairwise)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: e6:54:18:8a:97:71 WPA_PTK entering state PTKCALCNEGOTIATING
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: Searching a PSK for e6:54:18:8a:97:71 prev_psk=(nil)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: PTK derivation using PRF(SHA1)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: PTK derivation - A1=b8:27:eb:27:bd:07 A2=e6:54:18:8a:97:71
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Nonce1 - hexdump(len=32): 16 85 90 2f a7 96 3d 24 6f f8 55 5b 90 b2 7e 12 50 d4 38 5a 03 97 8d 85 0f b3 2c f6 36 9e 05 0d
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Nonce2 - hexdump(len=32): d5 f9 a4 80 6a 47 6a cf 2c 82 a6 6b 98 c5 6d 27 aa cd 1b 0b 80 9e 99 90 b6 88 49 e8 88 e2 03 57
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: PMK - hexdump(len=32): [REMOVED]
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: PTK - hexdump(len=48): [REMOVED]
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: KCK - hexdump(len=16): [REMOVED]
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: KEK - hexdump(len=16): [REMOVED]
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: TK - hexdump(len=16): [REMOVED]
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: EAPOL-Key MIC using HMAC-SHA1
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: e6:54:18:8a:97:71 WPA_PTK entering state PTKCALCNEGOTIATING2
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: e6:54:18:8a:97:71 WPA_PTK entering state PTKINITNEGOTIATING
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: hostapd_logger: STA e6:54:18:8a:97:71 - sending 3/4 msg of 4-Way Handshake
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Send EAPOL(version=2 secure=1 mic=1 ack=1 install=1 pairwise=1 kde_len=46 keyidx=1 encr=1)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Replay Counter - hexdump(len=8): 00 00 00 00 00 00 00 02
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: Plaintext EAPOL-Key Key Data - hexdump(len=56): [REMOVED]
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Encrypt Key Data using AES-WRAP (KEK length 16)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: EAPOL-Key MIC using HMAC-SHA1
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Use EAPOL-Key timeout of 1000 ms (retry counter 1)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: l2_packet_receive: src=e6:54:18:8a:97:71 len=135
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: l2_packet_receive: Drop duplicate RX
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: l2_packet_receive_br: src=b8:27:eb:27:bd:07 len=169
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wlan0: RX EAPOL from b8:27:eb:27:bd:07 to e6:54:18:8a:97:71 (bridge - not for this interface - ignore)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: l2_packet_receive: src=e6:54:18:8a:97:71 len=113
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wlan0: RX EAPOL from e6:54:18:8a:97:71 to b8:27:eb:27:bd:07 (bridge)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wlan0: RX EAPOL from e6:54:18:8a:97:71
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: IEEE 802.1X: 99 bytes from e6:54:18:8a:97:71
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: IEEE 802.1X: version=1 type=3 length=95
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Received EAPOL-Key from e6:54:18:8a:97:71 key_info=0x30a type=2 mic_len=16 key_data_length=0
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Received Key Nonce - hexdump(len=32): 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: Received Replay Counter - hexdump(len=8): 00 00 00 00 00 00 00 02
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: hostapd_logger: STA e6:54:18:8a:97:71 - received EAPOL-Key frame (4/4 Pairwise)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: EAPOL-Key MIC using HMAC-SHA1
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: WPA: e6:54:18:8a:97:71 WPA_PTK entering state PTKINITDONE
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wpa_driver_nl80211_set_key: ifindex=3 (wlan0) alg=3 addr=0x18feea8 key_idx=0 set_tx=1 seq_len=0 key_len=16
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: nl80211: KEY_DATA - hexdump(len=16): [REMOVED]
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: addr=e6:54:18:8a:97:71
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wlan0: P2P: Marking group formation completed on GO on first data connection
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: dbus: Register STA object '/fi/w1/wpa_supplicant1/Interfaces/3/Stations/e654188a9771'
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: dbus: STA signal StationAdded
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: dbus: Station MAC address 'e6:54:18:8a:97:71' 'StaAuthorized'
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: wlan0: AP-STA-CONNECTED e6:54:18:8a:97:71
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: nl80211: Set STA flags - ifname=wlan0 addr=e6:54:18:8a:97:71 total_flags=0x61 flags_or=0x1 flags_and=0xffffffff authorized=1
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: hostapd_logger: STA e6:54:18:8a:97:71 - authorizing port
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: hostapd_logger: STA e6:54:18:8a:97:71 - pairwise key handshake completed (RSN)
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: l2_packet_receive_br: src=e6:54:18:8a:97:71 len=113
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: l2_packet_receive_br: Drop duplicate RX
Dec 21 07:13:59 osmc-pi3 wpa_supplicant[362]: dbus: flush_object_timeout_handler: Timeout - sending changed properties of object /fi/w1/wpa_supplicant1/Interfaces/3
Dec 21 07:14:00 osmc-pi3 connmand[395]: DHCP server: Received DISCOVER
Dec 21 07:14:00 osmc-pi3 connmand[395]: DHCP server: find yiaddr 33597632
Dec 21 07:14:00 osmc-pi3 connmand[395]: DHCP server: lease_mac (nil) lease_nip (nil)
Dec 21 07:14:00 osmc-pi3 connmand[395]: DHCP server: Sending OFFER of 192.168.0.2
Dec 21 07:14:00 osmc-pi3 connmand[395]: DHCP server: Broadcasting packet to client
Dec 21 07:14:01 osmc-pi3 connmand[395]: DHCP server: Received DISCOVER
Dec 21 07:14:01 osmc-pi3 connmand[395]: DHCP server: find yiaddr 33597632
Dec 21 07:14:01 osmc-pi3 connmand[395]: DHCP server: lease_mac 0x1a88258 lease_nip 0x1a88258
Dec 21 07:14:01 osmc-pi3 connmand[395]: DHCP server: Sending OFFER of 192.168.0.2
Dec 21 07:14:01 osmc-pi3 connmand[395]: DHCP server: Broadcasting packet to client
Dec 21 07:14:01 osmc-pi3 connmand[395]: DHCP server: Received REQUEST NIP -1062731774
Dec 21 07:14:01 osmc-pi3 connmand[395]: DHCP server: Sending ACK
Dec 21 07:14:01 osmc-pi3 connmand[395]: DHCP server: Sending ACK to 192.168.0.2
Dec 21 07:14:01 osmc-pi3 connmand[395]: DHCP server: Broadcasting packet to client
Dec 21 07:14:01 osmc-pi3 connmand[395]: DHCP server: lease_mac 0x1a88258 lease_nip 0x1a88258
Dec 21 07:14:01 osmc-pi3 connmand[395]: src/inet.c:icmpv6_rs_event()
Dec 21 07:14:01 osmc-pi3 connmand[395]: src/inet.c:icmpv6_rs_recv()
Dec 21 07:14:01 osmc-pi3 connmand[395]: src/inet.c:icmpv6_rs_recv() code 0 len 16 hdr 8
Have you rebooted the rpi after your change?
I rebooted now after adding the debug flag to that service you mentioned
So I gather some logs, there’s plenty of them.
I’d analyze them later today but maybe you could take a look if you see something out of ordinary
I cannot paste them since they’re too big and also cannot include .txt file so here’s the pastebin: https://pastebin.com/nLBNxxWA
Like you I have not seen these logs before but I’ll have a short look at it later. Don’t count on me. Perhaps, others can shed some light what’s going wrong with your rpi.
Here is where it starts to behave different/starts failing in your logs compared to mine:
Dec 21 06:26:23 osmc wpa_supplicant[209]: hostapd_logger: STA 8c:f5:a3:99:f6:f8 - sending 3/4 msg of 4-Way Handshake
Dec 21 06:26:23 osmc wpa_supplicant[209]: WPA: Send EAPOL(version=2 secure=1 mic=1 ack=1 install=1 pairwise=1 kde_len=46 keyidx=1 encr=1)
Dec 21 06:26:23 osmc wpa_supplicant[209]: WPA: Replay Counter - hexdump(len=8): 00 00 00 00 00 00 00 03
Dec 21 06:26:23 osmc wpa_supplicant[209]: Plaintext EAPOL-Key Key Data - hexdump(len=56): [REMOVED]
Dec 21 06:26:23 osmc wpa_supplicant[209]: WPA: Encrypt Key Data using AES-WRAP (KEK length 16)
Dec 21 06:26:23 osmc wpa_supplicant[209]: WPA: EAPOL-Key MIC using HMAC-SHA1
Dec 21 06:26:23 osmc wpa_supplicant[209]: WPA: Use EAPOL-Key timeout of 1000 ms (retry counter 2)
Dec 21 06:26:24 osmc wpa_supplicant[209]: hostapd_logger: STA 8c:f5:a3:99:f6:f8 - EAPOL-Key timeout
During the WPA authentication (especially during the third phase of the 4-way handshake) there is no more response from the wifi client (timeout 1000 ms). There are 5 retries of this phase, then the code gives up (believing the log entries).
Whether something goes wrong on the client side (WPA and WPA2 enabled? WPA implementation buggy?) or the rpi (some bug in wpa_supplicant, wifi driver or wifi firmware), I cannot say.
What mobile device is it?
Hey
sorry for late reply
I changed WiFi password just to see if that changes anything, but sadly not
Mobile device is Samsung Galaxy S7, but I also use a laptop to connect, that’s a log from laptop attempt: https://pastebin.com/GyWZKksD
Maybe my raspberry is faulty
Maybe for another try I’ll use some other sdcard with something else installed like raspbian or whatever and see the thethering there, just to exclude or confirm hardware issue