Could you please link me to some information on the background of this claim? Or you refer to the CPU requirements for high bandwidth encryption?
I’m guessing a provider may have said this as a potential cop out as to why streams load slowly, knowing Kodi users focus on OpenVPN.
PPTP can be blocked / throttled very trivially by ISPs. OpenVPN will be performant, unless you run it on a very slow system.
We are working on OpenVPN integration with OSMC
After Stretch, it is my next area to make progress.
OpenVPN should provide you with adequate bandwidth. You won’t see protocol overhead, even in the tens of megabits.
No work is planned for PPTP
Sam
I’d just add that the UDP protocol is ideally suited to streaming video, since you can tolerate the odd dropped frame, and will often give you higher speeds than using TCP. Unfortunately, some ISPs will place a cap on continuous UDP traffic, so you might find that TCP gives significantly better performance.
DSL-Speed für Video-Streaming
Anbieter Mindestvoraussetzung HD-Qualität 4K-Qualität
Amazon 0,9 MBit/s 3,5 MBit/s 15 MBit/s
Maxdome 2 MBit/s 6 MBit/s nicht verfügbar
Netflix 0,5 MBit/s 5 MBit/s 25 MBit/s
Magine 2 MBit/s 8 MBit/s nicht verfügbar
Zattoo 4 MBit/s 7 MBit/s nicht verfügbar
TV SPIELFILM live 2 MBit/s 4 MBit/s nicht verfügbar
Sky Go 2 Mbit/s 6 MBit/s nicht verfügbar
There can be a 100 different reasons why OpenVPN might give poor speeds - and many of them are not the fault of OpenVPN.
What does a table of required streaming speeds (apparently taken from Video-Streaming: So schnell muss DSL für Netflix & Co. sein - CHIP ) have to do with the performance of OpenVPN?
Because these are the required speeds for HighQuality Streams.
I think i havent made that clear, so i make another try.
The Bandwith output depends on encryption depth and correlates with CPU. Yes it doesnt really matter for your Desktop PC, but in most cases OSMC is working on little machines like RaspberryPi or similar.
Even if you have the fastest VPN Provider (PP) with unlimited Bandwith and use a Pi3 as an OpenVPN Gateway that doesnt do anything else you only get 17-24MBits out of it.
If you make OpenVPN work on OSMC you will not get more, because you will run 4k Video on it too at the same time.
And thats why PPTP is better for OSMC. You will get high Bandwith and you dont need full encryption.
The Pi has two main shortcomings as far as OpenVPN throughput is concerned:
- a relatively slow ethernet connector that shares the USB bus;
- no hardware acceleration for AES encryption.
As far as the second point is concerned, you might be surprised by the figures (on a Pi 3):
osmc@osmc:~$ openssl speed aes-128-cbc
<snip>
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
aes-128 cbc 39545.79k 47180.76k 49610.50k 50413.91k 50645.67k
For the AES-128-CBC cipher, the CPU is able to encrypt 50 megabytes per second with a 1k block size. That’s 400 megabits per second. Clearly, there are other significant overheads with OpenVPN but it’s not as slow as you seem to think.
Here is the same test on a Vero4K:
osmc@osmc:~$ openssl speed aes-128-cbc
<snip>
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
aes-128-cbc 42325.40k 55580.25k 60183.38k 61385.39k 62100.29k
So 20% faster by default, plus the Vero4K doesn’t share its ethernet with the USB bus.
But if you look at this thread, you’ll see that the Vero4K is actually capable of:
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
aes-128-cbc 143775.92k 415486.72k 756965.46k 974767.10k 1064138.07k
That’s almost 1 gigabyte per second encryption with a 1k block. Would that be fast enough?
i dont know where you get those but on my Pi3 it looks different.
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
aes-128 cbc 28432.57k 33765.14k 35682.29k 36030.12k 36164.95k
and this is theoretically the output of 256 cbc.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
aes-256 cbc 22638.64k 25964.93k 26922.58k 27194.03k 27273.90k
On real connections there is more variation but mostly less than theory (Mbit)
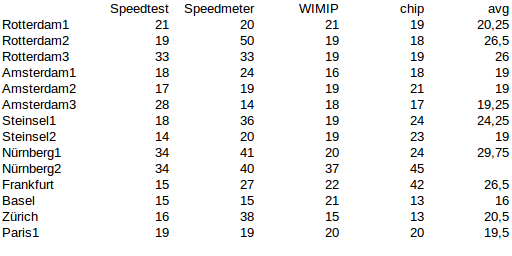
Its ok when u want to sell your vero and push this as a “payed feature”, but then make that clear and stop confusing people on telling them that there is a working solution for PPTP or that OpenVPN on a Pi has no Limits.
Hi,
Dilthedog did not suggest the pi3 had no limits for openvpn, just advised they were better than expected. My pi3 produced these results:
openssl speed aes-128-cbc:
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
aes-128 cbc 39668.55k 47030.76k 49528.49k 50323.46k 50528.26k
openssl speed aes-256-cbc:
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
aes-256 cbc 32052.38k 36668.59k 38229.08k 38638.59k 38726.31k
These concur with Dil’s results.
Tom
yes u are right. my result was caused by underclocking. My pi was running at only 1000Mhz.
I fixed it and it now runs on 1300Mhz wich results in:
openssl speed aes-128-cbc
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
aes-128 cbc 40871.02k 48798.53k 51406.34k 52102.14k 52281.34k
openssl speed aes-256-cbc
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
aes-256 cbc 32601.20k 37413.46k 38926.85k 39315.80k 39565.44k
But ive done some more testing in aes-128-cbc vs aes-256-cbc and got very interesting Results.
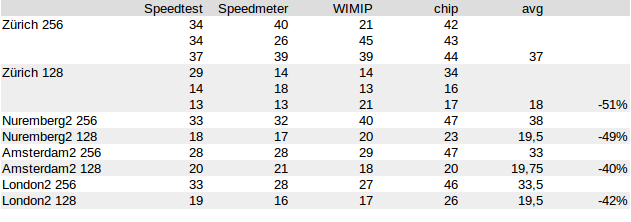
It looks like aes-128-cbc encryption is about 40 to 50 percent slower than 256 under real Conditions.