Dear all,
I have a Raspberry Pi3 connected via ethernet.
I have connman working to create a wifi hotspot tethered to the ethernet. I have added the route as described in Tethering and OpenVPN - #2 by matosch
iptables -t nat -A POSTROUTING -o tun0 -j MASQUERADE
It all works fine to connect my phone to the wifi created.
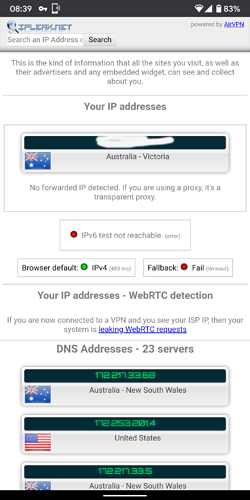
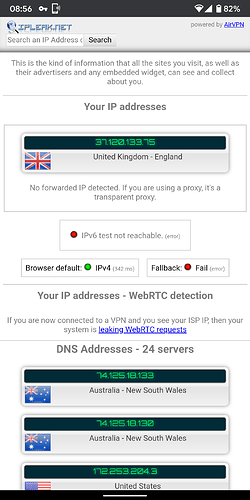
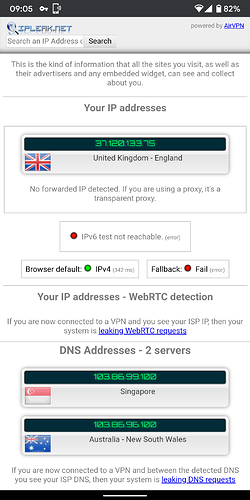
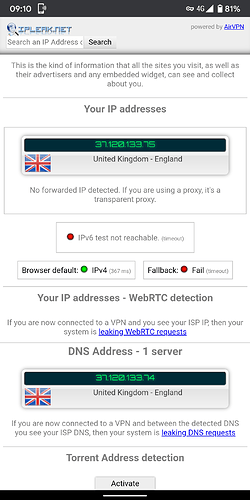
Now I added OpenVPN, and simply enough it works and ipinfo.io shows me in another country from both the Pi directly and the devices connected over wifi.
However, I would like to only route the wifi traffic over the VPN and leave the rest of ethernet traffic to go through my regular gateway so that I can SSH into my Pi from outside the network.
My attempts have included adding route-nopull and route 192.168.1.0 255.255.255.0 to my OpenVPN config as described here windows - OpenVPN: Only route a specific IP addresses through VPN? - Super User but it stops all traffic working on the devices over wifi.
I have messed around with the iptables a bunch but I think I am running out of trials to error.
How can I route all wifi traffic (192.168.1.*) through the established tun0 without affecting ethernet traffic?
I could live with all traffic going through the VPN if I can set a route to be able to access the Pi from outside the network, maybe this is easier?
Here are some outputs of relevant files in the working state: Please ask for more if it helps:
root@RaspberryPi:/# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.0.1 0.0.0.0 UG 0 0 0 eth0
10.8.2.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0
192.168.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
192.168.0.1 0.0.0.0 255.255.255.255 UH 0 0 0 eth0
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 tether
The route nat table:
root@RaspberryPi:/# iptables -L -t nat -n
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
connman-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0
Chain connman-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 192.168.1.0/24 0.0.0.0/0
Hope somebody can help, it’s driving me crazy. Thanks